08
JanReferential Integrity in DBMS With Example
Integrity constraints in DBMS are rules that ensure the accuracy and consistency of data in a database. These constraints help in maintaining valid relationships between tables and prevent invalid data from being entered. By applying integrity constraints in DBMS, we can protect the quality of data and enforce business rules within the system. They are especially important when managing large and complex databases.
In the DBMS tutorial, understanding integrity constraints in DBMS is key to designing secure and reliable databases.
What are Integrity Constraints in DBMS?
Integrity constraints in DBMS are rules that ensure data in a database is accurate and consistent. They prevent invalid or unwanted data from being stored. These constraints help maintain the reliability and correctness of the database.
Types of Integrity Constraints
- Domain Constraints
- Not-Null Constraints
- Entity integrity Constraints
- Key Constraints
- Primary Key Constraints
- Referential integrity constraints
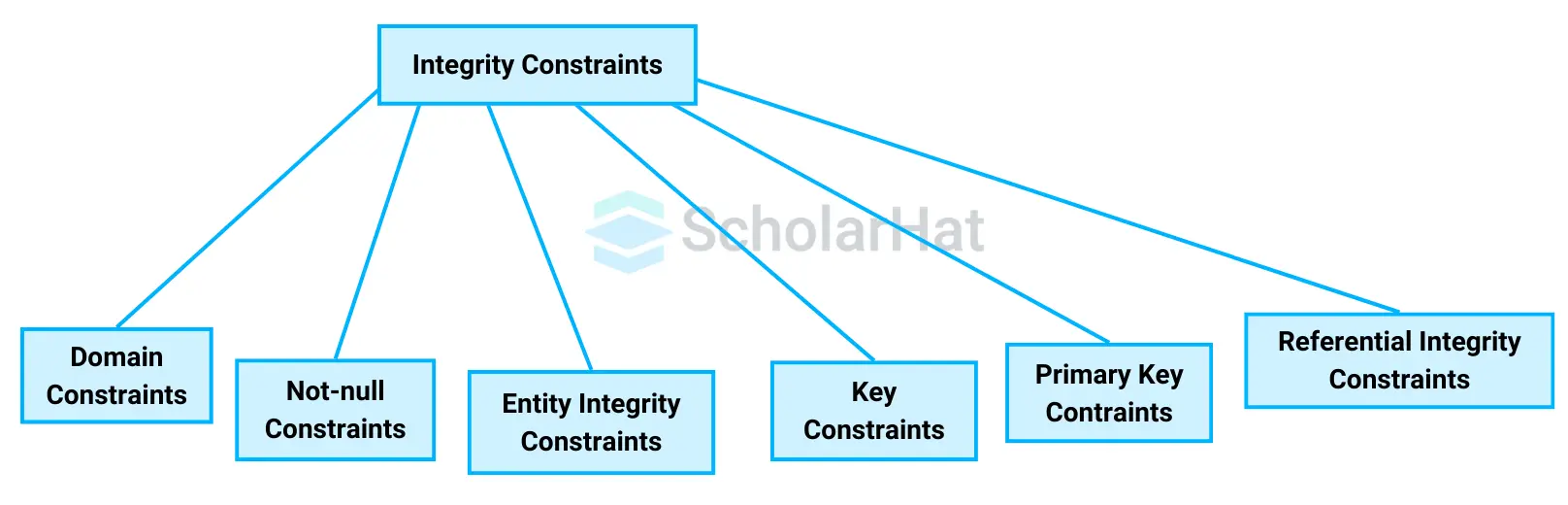
Note: In this article, we will only learn about Referential Integrity Constraints.
Read More: |
What are Referential Integrity Constraints?
Referential Integrity in DBMS ensures that the relationship between tables remains logical. When a table has a foreign key that references the primary key of another table, referential integrity ensures that this foreign key value always refers to an existing, valid row in the referenced table.
Key Aspects of Referential Integrity
Here are the crucial aspects of referential integrity constraints:
- Primary Keys
- Foreign Key
- Relationship between Tables
- Primary Keys
The primary keys in DBMS are columns or combinations of columns that unequally identify each row of the data. The primary key provides some features.
- Uniqueness: Each record must have a unique primary key value.
- Not Null: A primary key cannot contain null values.
- Minimal: The primary key should be as small as possible for performance reasons.
Example
In this example, we are creating a table named Student with the syntax:
| CREATE TABLE Student (Student_Id int Primary Key, Student_Name varchar(25) ); |
Student Table
| Student_Id | Student_Name |
| 101 | Rakesh |
| 102 | Ayansh |
| 103 | Ankita |
| 104 | Anusha |
In the above example, Student_Id is the primary key.
- Foreign Keys
The foreign key refers to a column or combination of columns that is used to establish and enforce a link between the data in two tables to control the data that can be stored in the foreign key table.
Example
In this example, we are creating a Course table that is referenced by the Student table. The syntax for that table:
| CREATE TABLE Course ( Student_Id int references Student, Student_Section int, Student_Course varchar(10) ); |
Course Table
| Student_Id | Student_Section | Student_Course |
| 101 | 1 | MCA |
| 102 | 2 | BCA |
| 103 | 2 | BCA |
| 104 | 1 | MCA |
In this example, Student_Id becomes a foreign key after being referenced by the Student table.
- Relationship between tables
Referential integrity is the most important concept in database management. That ensures the relationship between tables remains consistent. It is managed by a foreign key that links rows in one table to rows in another. Here are the relationships between tables in referential integrity;
1. One-to-One (1-1) Relationship: A one-to-one relationship occurs when a single record in one table correlates to exactly one record in another table.
Example
Table A ( Student )
| Student_Id | Student_Name |
| 101 | Ankita |
| 102 | Aman |
| 103 | Anurag |
Table B ( Course )
| Student_Id | Course | Address |
| 101 | BCA | Mumbai |
| 102 | BCA | Delhi |
| 103 | MCA | Kolkata |
In the Student table, the primary key is the Student_Id, and in the Course table, the Student_Id is the foreign key and primary key, both of which define the One-to-One relationship in the table.
2. One-to-Many (1-M) Relationship: A one-to-many relationship occurs when a single record in one table can correlate to multiple records in another table, but a record in the second table can only correspond to one record in the first.
Example
Table A (Student)
| Student_Id | Student_Name |
| 101 | Aman |
| 102 | Ankita |
| 103 | Anurag |
Table B (RollNumber)
| Student_Id | Course | Student_Roll |
| 101 | BCA | 01 |
| 102 | BCA | 02 |
| 103 | BCA | 03 |
In the given example, The foreign key is the Student_Id, and Student_Roll is the primary key. This key defines the possibility that multiple students can pursue the same course, showing One-to-Many relationships.
3. Many-to-Many (M-M) Relationship: A many-to-many relationship occurs when multiple records in one table are correlated with multiple records in another table. This kind of record can't be directly implemented using only two tables and requires a third table called a junction table or join table.
Example
Student Table
| Student_Id | Student_Name |
| 101 | Aman |
| 102 | Ankita |
| 103 | Anurag |
Course Table
| Course_Id | Course_Name |
| 1001 | Java |
| 1002 | Python |
| 1003 | C++ |
Enrollment Table
| Student_Id | Course_Id | Course_name |
| 101 | 1001 | Java |
| 101 | 1003 | C++ |
| 102 | 1002 | Python |
| 102 | 1001 | Java |
| 103 | 1002 | Python |
In this example, we saw that multiple students could enroll in multiple courses, which shows the many-to-many relationships.
Guaranteeing Referential Integrity
Guaranteeing referential integrity in a database is most important for managing the accuracy and consistency of data in related tables. Here are the key steps and methods for ensuring referential integrity;
Creating Foreign Key Constraints
We create foreign key constraints to link tables. This means that every foreign key value must match an existing primary key value in the referenced table.
Use Cascading Actions
Cascading actions in a DBMS are rules applied to maintain referential integrity when a primary key in the parent table is updated or deleted.
1. ON DELETE CASCADE
It refers to an operation in which when a row in the parent table is deleted, all related rows in the child table are also deleted.
2. ON UPDATE CASCADE
It refers to an operation in which when we update the primary key value in the parent table, all corresponding foreign key values in the child table are also updated.
Referential Integrity Constraints
Referential integrity constraints refer to the validity of the relationship between data in multiple tables and the fact that the data is not lost or orphaned.
Advantages of Managing Referential Integrity
There are several benefits of maintaining the referential integrity that are depicted below;
Data Accuracy
- Implement checks and validation rules to ensure data entered into the database meets the standard.
- Continuously run scripts to identify and correct errors in the database.
Data Consistency
- Ensure the database transactions are atomic, meaning they are fully completed or fully rolled back, preventing partial updates.
- Structure the database to remove redundancy and ensure logical data storage, reducing the risk of anomalies.
Avoiding Orphan Records
- Using foreign key constraints to ensure that the child table records reference valid primary key records in the parent table.
- Using triggers to validate foreign key relationships before inserting or updating records and handling related child records when a parent record is deleted.
Common Issues and Challenges
Managing referential integrity in DBMS can be challenging due to various issues and complexity. Here are some common problems;
- Unintentional data loss due to cascading deletes and updates.
- Difficulty in handling circular references between tables.
- Complications in data insertions, updates, and deletes.
- Impact on performance due to enforcing referential integrity constraints.
- Risk of orphan records if constraints are not properly enforced.
Best Practices for Managing Referential Integrity
The various best practices for maintaining referential integrity are as follows;
- Design the database schema carefully
- Use appropriate constraints
- Implement data validation
- Regularly integrity checks
- Use triggers for complex integrity rules
Tools and Techniques Used in Referential Integrity
There are several tools and technologies used in referential integrity:
- Database Management System (DBMS)
- Structured Query Language(SQL)
- Database Design Tools(Visual Tools)
- ORM Framework
- Data Quality Tools
Conclusion
In conclusion, integrity constraints in DBMS are important rules that help keep the data correct, complete, and meaningful. They make sure only valid data goes into the database and stop wrong or duplicate entries. This helps in keeping the database well-organized and easy to use. Without these rules, it would be hard to trust the data or maintain relationships between different parts of the database.
ScholarHat provides various Training and Certification Courses to help you in your end-to-end product development: |
FAQs
- Database-Specific Checks
- SQL Queries
- Data Quality Tools
- Database Monitoring and Auditing
- ON DELETE CASCADE- When a row in the parent table is deleted, all related rows in the child table are also deleted.
- ON UPDATE CASCADE- When a primary key value in the parent table is updated, all corresponding foreign key values in the child table are also updated.
- Distributed transactions
- Eventual consistency
- Application level enforcement
- Data replications
Take our Dbms skill challenge to evaluate yourself!

In less than 5 minutes, with our skill challenge, you can identify your knowledge gaps and strengths in a given skill.