18
AprWhat is Kubernetes Architecture?
Kubernetes Architecture
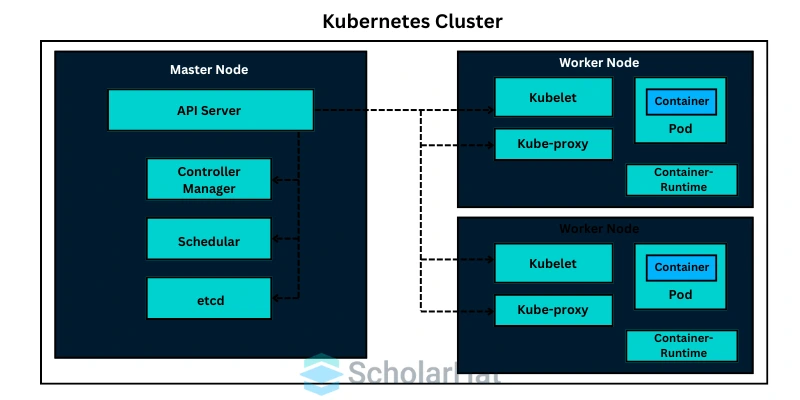
Kubernetes is an open-source container orchestration platform designed to automate the deployment, scaling, and management of containerized applications. Kubernetes architecture is divided into two main parts:
- 1. Control Plane (Master Node): The brain of Kubernetes, responsible for managing the cluster. It includes components like the API Server, Scheduler, Controller Manager, etcd (key-value store).
- 2. Worker Nodes: The machines where containers are deployed. Each node runs a kubelet (agent), kube-proxy (networking), and a container runtime (e.g., Docker).
It is also called Kubernetes cluster architecture. Understanding Kubernetes cluster architecture is essential for deploying and managing containerized applications at scale.
This is just a short trailer if you are looking,
- To understand Kubernetes architecture by grasping the fundamental concepts behind its components.
- To learn about the key architectural components of Kubernetes.
- To explore how these components interact and work together through various workflows.
| Note: In case you came here for Kubernetes Interview Preparation, then you can consider our Kubernetes Interview Questions for Freshers and Advanced Professionals article. |
This Kubernetes Tutorial will be helpful for you if you are a beginner and want to know an in-depth overview of how Kubernetes works, so stay tuned, and let's explore what Kubernetes architecture is in depth. But before this, you need to understand some prerequisites.
Prerequisites to Learning Kubernetes Architecture
To understand Kubernetes architecture, you need a solid foundation in the following areas:
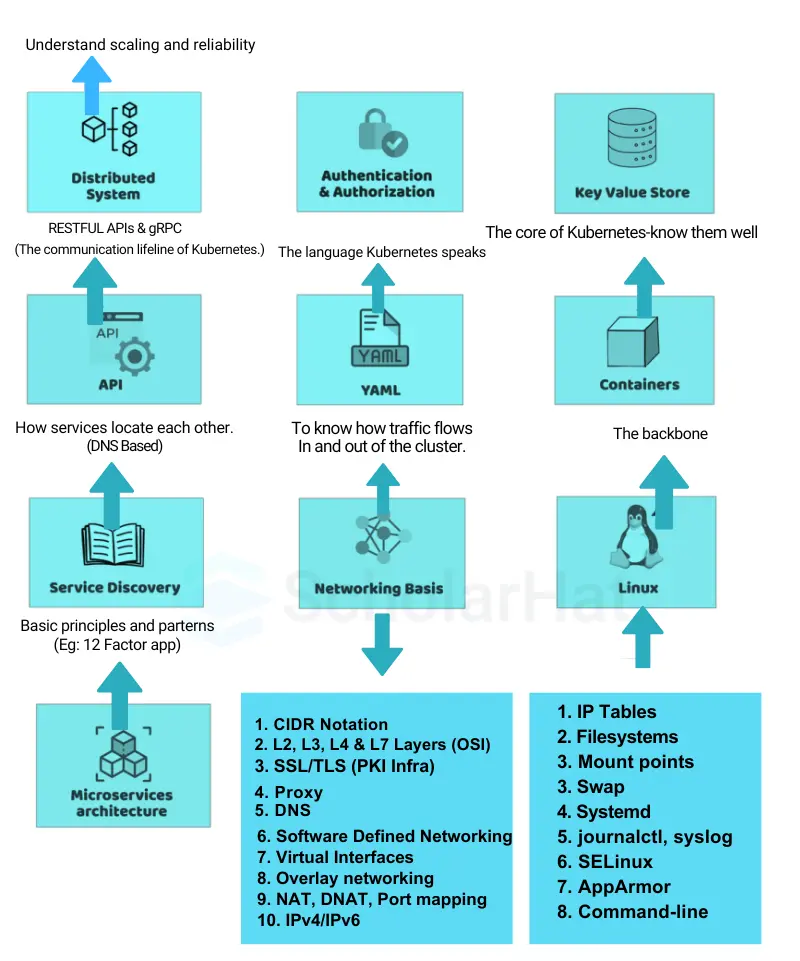
1. Containers:
- Learn container basics and gain hands-on experience with tools like Docker or Podman.
- Understand the Open Container Initiative (OCI) and Container Runtime Interface (CRI).
2. Distributed Systems:
- Learn the basics of distributed systems and their use cases in modern IT infrastructure.
- Familiarize yourself with the CAP theorem.
3. Authentication & Authorization:
- Understand the basics of authentication (who you are) and authorization (what you can do).
4. Key-Value Store:
- Learn the basics of NoSQL databases, particularly key-value stores like etcd.
5. API:
- Understand RESTful APIs and gRPC APIs, as Kubernetes is API-driven.
6. YAML:
- Learn YAML syntax, as it is used for Kubernetes configuration files.
7. Service Discovery:
- Understand client-side and server-side service discovery mechanisms.
8. Networking Basics:
- Learn about CIDR notation, IP addresses, OSI layers (L2, L3, L4, L7), SSL/TLS, proxies, DNS, IPVS/IPTables, and overlay networking.
9. Linux:
- Gain knowledge of Linux concepts like IPTables, filesystems, mount points, systemd, journalctl, SELinux, and AppArmor.
What is Kubernetes Architecture
The Kubernetes cluster architecture consists of a Control Plane and Worker Nodes, each with distinct roles and responsibilities
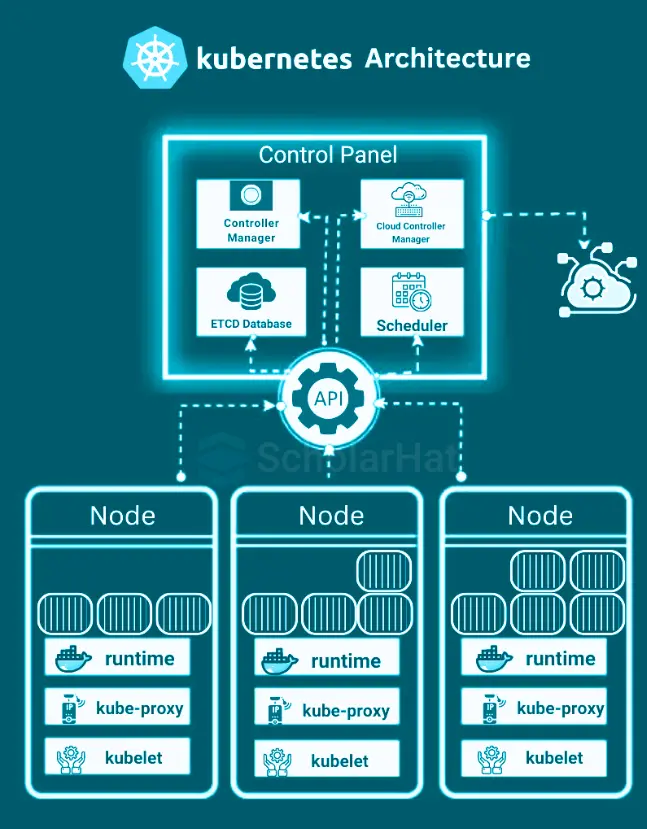
1. Control Plane (Master Node Components)
In Kubernetes cluster architecture, the Control Plane manages the cluster state, while Worker Nodes execute application workloads
a. API Server (kube-apiserver)
- A key component of Kubernetes cluster architecture is the API Server, which acts as the central hub for all cluster communications or acts as the front-end for Kubernetes.
- Exposes Kubernetes API using RESTful endpoints.
- Serves as the primary communication hub between internal components and external clients.
- Implements authentication, authorization, and admission control mechanisms.
b. Controller Manager (kube-controller-manager)
- Ensures the cluster is in the desired state by running multiple controller processes.
- Key controllers include:
- Node Controller: Monitors the health of worker nodes.
- Replication Controller: Ensures the correct number of pod replicas.
- Service Account & Token Controller: Manages service accounts and tokens.
c. Scheduler (kube-scheduler)
- Assign pods to worker nodes based on available resources, affinity, taints, and tolerations.
- Uses scheduling algorithms to optimize workload distribution.
d. etcd
- The etcd database plays a critical role in Kubernetes cluster architecture by storing the cluster's configuration and state data.
- A distributed key-value store that acts as the cluster's backing store.
- Stores cluster configuration, state, and metadata.
- Kubernetes cluster architecture ensures high availability by allowing multiple instances of Control Plane components to run in parallel using a consensus algorithm (Raft).
e. Cloud Controller Manager (optional):
- It integrates with cloud provider APIs to manage cloud-specific resources (e.g., load balancers, storage volumes).
2. Worker Node Components
Worker Nodes in Kubernetes cluster architecture are responsible for running Pods, which are the smallest deployable units in Kubernetes.. Each worker node runs several key components:
a. Kubelet
- An agent that runs on each worker node.
- Communicates with the API Server to receive and execute pod definitions.
- Ensures that containers are running as expected.
b. Kube-Proxy
- Manages networking for Kubernetes services.
- Implements network rules for inter-pod communication using iptables or IPVS.
- Enables external access to Kubernetes services.
c. Container Runtime
- The software is responsible for running containers on worker nodes.
- Supports various runtimes like Docker, containerd, and CRI-O.
3. Kubernetes Networking Model
Networking and storage are integral parts of Kubernetes cluster architecture, enabling seamless communication and data persistence.
- Pod-to-Pod Communication: Uses flat networking, where each pod gets a unique IP.
- Pod-to-Service Communication: Services expose stable endpoints to route traffic.
- External Access: Load balancers, Ingress controllers, and NodePort services allow external connectivity.
4. Kubernetes Storage Model
Persistent storage in Kubernetes is handled using:
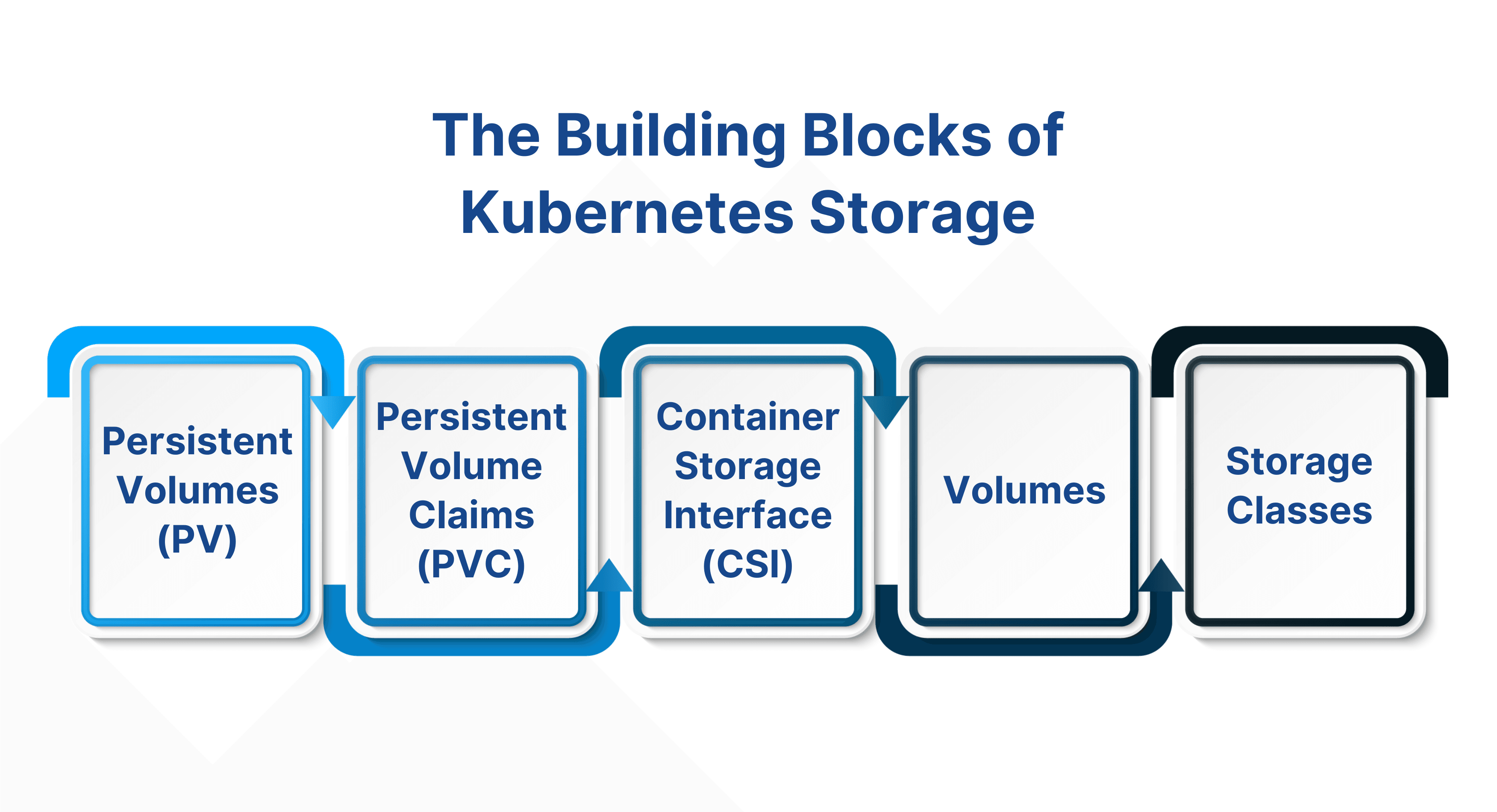
- Volumes: Temporary storage attached to pods.
- Persistent Volumes (PV): Independent storage lifecycle, provisioned manually or dynamically.
- Persistent Volume Claims (PVC): Requested by applications to bind to PVs.
Kubernetes Extensibility
Kubernetes cluster architecture supports extensibility through add-ons like CNI plugins, CSI plugins, and ingress controllers.
Extensibility Mechanisms:
- Custom Resource Definitions (CRDs):
- Allow users to define their own resource types (e.g., custom objects) in addition to built-in resources like Pods, Services, and Deployments.
- Used by operators to automate application management.
- Operators:
- Kubernetes-native applications that use CRDs to manage complex, stateful applications (e.g., databases, message queues).
- Automate tasks like backups, scaling, and updates.
- API Aggregation:
- Enables the addition of custom APIs to the Kubernetes API Server.
- Useful for integrating external services or adding custom functionality.
- Admission Controllers:
- Intercept requests to the API Server to enforce policies, validate resources, or mutate requests (e.g., Pod Security Policies, Resource Quotas).
- Plugins:
- Kubernetes supports plugins for networking (CNI), storage (CSI), and device management (Device Plugins).
Kubernetes Addons/Plugins
Addons and plugins extend Kubernetes functionality, enabling users to customize and enhance their clusters. These tools are not part of the core Kubernetes distribution but are essential for advanced use cases.
Types of Addons/Plugins
1. Networking Plugins (CNI - Container Network Interface)
Kubernetes relies on CNI plugins to provide networking capabilities for Pods.
- Popular CNI Plugins:
- Calico: Provides networking and network policy enforcement.
- Flannel: A simple overlay network for Kubernetes.
- Weave: Offers networking and network policy features.
- Cilium: Focuses on security and observability using eBPF.
- Key Features:
- Pod-to-Pod communication.
- Network segmentation using Network Policies.
- Integration with cloud providers for LoadBalancer and Ingress.
2. Storage Plugins (CSI - Container Storage Interface)
CSI plugins enable Kubernetes to integrate with external storage systems.
- Popular CSI Plugins:
- AWS EBS: Provides block storage for AWS.
- GCP Persistent Disk: This offers storage for Google Cloud.
- Ceph RBD: Open-source distributed storage.
- Longhorn: Lightweight, distributed block storage for Kubernetes.
- Key Features:
- Dynamic provisioning of Persistent Volumes (PVs).
- Support for snapshots, cloning, and resizing of volumes.
3. Monitoring and Logging Addons
These add-ons help monitor cluster health and log application activity.
- Popular Tools:
- Prometheus: A monitoring and alerting toolkit.
- Grafana: Visualization tool for metrics collected by Prometheus.
- Fluentd/Elasticsearch/Kibana (EFK): Logging stack for collecting, storing, and visualizing logs.
- Key Features:
- Real-time monitoring of cluster metrics (e.g., CPU, memory, disk usage).
- Centralized logging for troubleshooting and auditing.
4. Security Addons
These addons enhance the security of Kubernetes clusters.
- Popular Tools:
- Falco: Runtime security tool for detecting anomalous behavior.
- Kyverno: Policy engine for enforcing security policies.
- OPA Gatekeeper: Policy controller for enforcing custom policies.
- Key Features:
- Runtime threat detection.
- Policy enforcement for resource creation and modification.
5. Service Mesh Addons
Service meshes provide advanced networking features for microservices.
- Popular Tools:
- Istio: Offers traffic management, security, and observability.
- Linkerd: Lightweight service mesh for Kubernetes.
- Consul Connect: This is a Service mesh by HashiCorp.
- Key Features:
- Traffic routing and load balancing.
- Mutual TLS for secure communication.
- Observability (e.g., tracing, metrics).
6. Ingress Controllers
Ingress controllers manage external access to services in a cluster.
- Popular Ingress Controllers:
- NGINX Ingress Controller: Widely used for HTTP/HTTPS routing.
- Traefik: Modern ingress controller with dynamic configuration.
- HAProxy: High-performance ingress controller.
- Key Features:
- SSL/TLS termination.
- Load balancing and path-based routing.
Kubernetes and Security
Security is a fundamental aspect of Kubernetes cluster architecture, with features like RBAC, Network Policies, and Secrets Management.
Key Security Features:
- Role-Based Access Control (RBAC):
- Restricts access to Kubernetes resources based on roles and permissions.
- Ensures that users and applications have the least privilege necessary.
- Network Policies:
- Define how Pods can communicate with each other and external networks.
- Enforces network segmentation and reduces the attack surface.
- Secrets Management:
- Stores sensitive information (e.g., passwords, tokens) securely.
- Can be encrypted at rest using etcd encryption.
- Pod Security Policies (PSPs):
- Enforces security settings for Pods (e.g., running as non-root, restricting privilege escalation).
- Audit Logging:
- Tracks all requests to the API Server for auditing and compliance purposes.
- Image Security:
- Ensures that only trusted container images are deployed (e.g., using image signing and scanning tools).
Best Practices for Kubernetes Security:
- Regularly update Kubernetes and its components to patch vulnerabilities.
- Use namespaces to isolate workloads and limit blast radius.
- Enable network encryption (e.g., TLS for API Server communication).
- Monitor and log cluster activity for suspicious behavior.
Commands for Kubectl
kubectl is the command-line tool for interacting with Kubernetes clusters. Below is an in-depth overview of commonly used kubectl commands and their purposes.
Basic Commands
1. Cluster Interaction
- Check Cluster Status:
Displays information about the cluster, including the API server address.kubectl cluster-info - Get Nodes:
kubectl get nodes
2. Resource Management
- Create Resources:
kubectl create -f <filename.yaml> - Apply Resources:
kubectl apply -f <filename.yaml> - Delete Resources:
kubectl delete -f <filename.yaml>
3. Viewing Resources
- List Pods:
kubectl get pods - List Services:
kubectl get services - Describe Resources:
kubectl describe pod <pod-name>
4. Debugging and Logs
- View Pod Logs:
kubectl logs <pod-name> - Execute Commands in a Pod:
kubectl exec -it <pod-name> -- /bin/sh - Port Forwarding:
kubectl port-forward <pod-name> <local-port>:<pod-port>
Advanced Commands
5. Scaling Resources
- Scale a Deployment:
kubectl scale deployment <deployment-name> --replicas=<number>
6. Rolling Updates and Rollbacks
- Rolling Update:
kubectl set image deployment/<deployment-name> <container-name>=<new-image> - Rollback a Deployment:
kubectl rollout undo deployment/<deployment-name>
7. Resource Management
- Edit Resources:
kubectl edit deployment <deployment-name> - Patch Resources:
kubectl patch deployment <deployment-name> -p '{"spec":{"replicas":3}}'
8. Namespaces
- Switch Namespace:
kubectl config set-context --current --namespace=<namespace-name>kubectlcommands. - List Namespaces:
kubectl get namespaces
9. Resource Quotas and Limits
- Get Resource Quotas:
kubectl get resourcequotas - Set Resource Limits:
# Example in a Pod definition resources: limits: cpu: "1" memory: "512Mi" requests: cpu: "0.5" memory: "256Mi"
10. Useful Tips
- Alias for Kubectl:
alias k=kubectlkfor faster usage. - Auto-Completion:
source <(kubectl completion bash)kubectlcommands in Bash.
Weak Points of Kubernetes Architecture
Despite its strengths, Kubernetes has some architectural weaknesses and challenges:
1. Complexity
- Kubernetes is inherently complex, with a steep learning curve.
- Managing and troubleshooting a Kubernetes cluster requires deep expertise.
2. etcd Bottleneck
- etcd is a critical component, and its performance can become a bottleneck in large clusters.
- etcd is sensitive to network latency and requires careful tuning for high availability.
3. Networking Challenges
- Kubernetes networking can be complex to configure and manage, especially in multi-cloud or hybrid environments.
- Network policies may not be enforced consistently across different CNI plugins.
4. Scalability Limitations
- While Kubernetes is designed to scale, very large clusters (e.g., thousands of nodes) can face performance issues.
- The API Server and etcd may struggle to handle high volumes of requests.
5. Security Risks
- Misconfigurations (e.g., overly permissive RBAC rules, exposed dashboards) can lead to security breaches.
- Default settings may not be secure, requiring additional hardening.
6. Resource Overhead
- Running Kubernetes introduces additional resource overhead (e.g., control plane components, networking plugins).
- Small clusters or lightweight workloads may not justify the overhead.
7. Stateful Workloads
- Managing stateful applications (e.g., databases) in Kubernetes can be challenging.
- Requires careful configuration of storage (e.g., Persistent Volumes) and backup strategies.
8. Vendor Lock-In
- While Kubernetes is open-source, relying on cloud-specific extensions or services can lead to vendor lock-in.
Conclusion
Kubernetes architecture is robust and flexible for container orchestration, but it comes with its own set of challenges. Understanding the architecture, extensibility, security features, and weaknesses is crucial for effectively deploying and managing Kubernetes clusters. By addressing these weak points and following the above-mentioned best practices, organizations can harness the full potential of Kubernetes while minimizing risks. Also, don't forget to consider our Docker and Kubernetes Certification Training, which covers containerization with Docker and orchestration with Kubernetes. Participants gain hands-on experience deploying and managing containerized applications.