26
AprSecurity Architecture in Cloud Computing
Security Architecture
Cloud security architecture is nothing but creating and implementing security controls, guidelines, and protocols to safeguard cloud-based data and systems. To provide safe access, data security, and adherence to laws and industry standards, it includes a variety of tactics and technology.
In this Azure tutorial, We will learn all about Security Architecture in Cloud Computing which will include Key Components of Cloud Security Architecture, Best Practices for Building a Secure Cloud Environment, etc. If you want to become a Certified Azure Developer don't forget to consider our Azure Developer Certification Training.
What is Security Architecture?
- A company's security infrastructure can be designed and constructed using an approach known as security architecture.
- It examines systems, processes, and controls to identify and fix problems related to data protection. N
- The Security architecture helps to manage risk management, security policy, and the selection of controls and processes.
- It is used to ensure network security, application security, or business information security,
Security Architecture Types
1. Network Security Architecture
- It is the step-by-step planning and execution of security measures to protect a company's computer networks from unauthorized access, cyberattacks, and data breaches.
- To safeguard the integrity and confidentiality of data transferred over a network, firewalls, intrusion detection/prevention systems, and other network security controls must be installed.
- For example, a company installs a network security architecture that includes firewalls, intrusion detection/prevention systems, and secure Wi-Fi protocols to protect its internal network from unauthorized access and cyber threats.
2. Application Security Architecture
- It is used to stop risks and unauthorized access, with its structured design and integration of security measures into software applications.
- Apps that process sensitive data must guarantee the confidentiality and integrity of that data using secure coding techniques, authentication protocols, and encryption.
- For example, a software development company incorporates safe coding techniques, encryption, and stringent authentication procedures into its application development process to avert vulnerabilities and protect user data.
3. Cloud Security Architecture
- Specifically, customized security guidelines and procedures are designed and implemented for cloud computing systems.
- Cloud-hosted data, apps, and infrastructure are protected by identity and access management (IAM), encryption, and regular security assessments.
- For example, an organization deploys resources in a cloud environment using identity and access management (IAM) limitations, encryption, and regular security audits to safeguard data and applications hosted on cloud platforms like Microsoft Azure and Amazon Web Services (AWS).
4. Enterprise Information Security Architecture
- The Enterprise Information Security Architecture (EISA) is a thorough approach to safeguarding the technological, procedural, and human resources of a company.
- To connect security efforts with business objectives and offer a unified security posture, it involves identity management, risk assessment, and the development and execution of comprehensive security policies.
- For example, a large financial institution creates an enterprise-wide security architecture that includes comprehensive security policies, identity management systems, and frequent risk assessments in order to safeguard sensitive customer information and guarantee regulatory compliance.
5. Wireless Security Architecture
- The design and execution of security measures for wireless networks are the focus of wireless security architecture.
- To guard data transit in Wi-Fi networks and stop unwanted access, it has features including access control, MAC address filtering, and WPA3 encryption.
- For example, to safeguard the Wi-Fi network and stop illegal access, the school uses a wireless security architecture that consists of WPA3 encryption, MAC address filtering, and access access.
6. Endpoint Security Architecture
- This architecture creates and puts into place security measures to guard particular devices, or "endpoints," such as laptops, smartphones, and tablets.
- To stop malware and unwanted access, it consists of mobile device management (MDM) programs, antivirus software, and endpoint detection and response (EDR) technologies.
- For example, to safeguard personal devices (computers, smartphones, etc.) against malware, mobile devices (MDM), and unwanted access, a corporation employs endpoint security measures, such as antivirus software, endpoint detection and response (EDR) tools, and networking solutions.
Key Components of Cloud Security Architecture
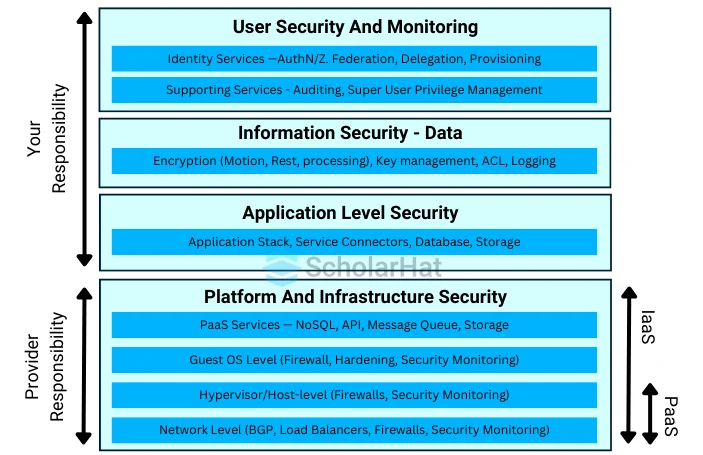
1. Management of Identity and Access (IAM)
- IAM is the cornerstone of cloud security.
- It controls access permissions and user identities.
- It guarantees that resources can only be accessed by authorized people and devices.
- Important procedures consist of Multiple factors of verification are required with Multi-Factor Authentication (MFA), which improves security.
- Reduces the possibility of unwanted access by assigning permissions based on user roles through the use of role-based access control (RBAC).
2. Security of Networks
It is essential to safeguard the network infrastructure. Among the network security measures are:
- A virtual private cloud (VPC) improves security by isolating network activity inside a virtual network.
- Security groups and firewalls manage traffic entering and leaving resources.
- Systems for detecting and preventing intrusions (IDPS) keep an eye on suspicious network activity and take appropriate action.
3. Data Encryption and Security
It is crucial to secure data both in transit and at rest. Technologies and procedures used in encryption include:
- Encryption at Rest: Encrypts information kept on databases and drives.
- Encryption in Transit: Using TLS/SSL protocols, encryption safeguards data while it moves across networks.
4. Security of Endpoints
protects endpoints and gadgets making cloud connections. This comprises:
- Stop harmful software from infecting endpoints with antivirus and anti-malware solutions.
- Endpoint detection and response, or EDR, keeps an eye on endpoint threats and takes appropriate action.
5. Security of Applications
Security of Applications makes sure apps are safe from the time they are developed until they are deployed. Important procedures consist of:
- Using secure coding practices means putting security measures in place while developing applications.
- Application firewalls: defend against web-based attacks including cross-site scripting (XSS) and SQL injection.
6. Governance and Compliance
Governance and Compliance ensure that best practices and legal requirements are followed. This includes:
- Tools for Compliance Management: Automate reporting and compliance assessments.
- Policy Management: Establishes and upholds security guidelines throughout the cloud infrastructure.
Examples of Security Architecture Framework
- Open Group Architecture Framework (TOGAF)
- Sherwood Applied Business Security Architecture (SABSA)
- Zachman Framework
- NIST Cybersecurity Framework
- ISO/IEC 27001
- MITER ATT&CK Framework
Why do we need security architecture?
- Risk mitigation: It is the process of identifying, evaluating, and reducing risks to the information assets of a company. Establish a system of security policies, controls, and processes to thwart cyberattacks and illegal access as part of comprehensive defense.
- Business Integration: Align security protocols with operational goals, offer security assistance, and accomplish organizational goals.
- Resource efficiency: This can be attained by ranking security measures according to risk assessment and business priority.
- Proactive defense: Defend the organization proactively against evolving cyberthreats, enhancing its capacity to handle unexpected events.
- Incident Response: Enhance the organization's capacity to react to security incidents in a way that minimizes loss of money and reputation.
- Regulatory Compliance: Assist companies in adhering to rules and ethical guidelines to prevent fines and other consequences.
Best Practices for Building a Secure Cloud Environment
1. Adopt a Model of Zero Trust
- The zero-trust security approach operates under the assumption that external and internal network threats may exist. Strict access controls and ongoing identity verification of users and devices are emphasized.
2. Put Security Automation Into Practice
- Reduce human mistakes and increase efficiency by automating security procedures.
- Patch management, incident response, and threat detection are among the activities that automated systems can perform.
3. Update and patch systems frequently
- Updating programs and systems is essential for preventing known vulnerabilities.
- To guarantee timely updates, put in place a strong patch management mechanism.
4. Keep an eye on and record activity
- Threats are identified and dealt with swiftly in cloud environments because of constant monitoring and logging of all activity.
- For centralized logging and analysis, use solutions such as Security Information and Event Management (SIEM) systems.
5. Perform recurring evaluations and audits of security
- To find and fix security flaws, conduct routine penetration tests, vulnerability assessments, and security audits.
- Recruit outside security professionals to do thorough evaluations.
6. Train and Educate Staff
- Give staff members regular security awareness and training sessions.
- Inform them about social engineering, phishing scams, and safe cloud usage techniques.
Conclusion
In cloud computing, creating a strong security architecture is important for defending against a constantly changing threat landscape. Organizations can boost their security posture, guarantee compliance, and protect their vital assets by implementing security architecture measures. To gain a deeper comprehension of more Azure fundamentals, take a look at our Azure Certification (Az-104) course.
FAQs
- IAM.
- Network and device security.
- Security monitoring/alerting.
- Governance.
- Disaster recovery and business continuity planning.
- Legal compliance.
Take our Devops skill challenge to evaluate yourself!

In less than 5 minutes, with our skill challenge, you can identify your knowledge gaps and strengths in a given skill.